ISO 27001 | Information Security
Achieve ISO 27001 certification, annual surveillance audits and recertification with expert support
ISO 27001 is the globally recognised standard for information security management systems (ISMS). It helps organisations safeguard sensitive data, minimise cybersecurity threats, and ensure confidentiality, integrity, and availability of data.
At Candy Management Consultants, we guide organisations to harness the full potential of ISO 27001 – transforming cybersecurity complexity into strategic resilience. We don’t deliver generic toolkits – we help you identify security gaps, implement robust controls, and prepare for successful certification audits.
Discover how the ISO 27001 standard can strengthen your organisation’s data protection and reduce cyber risk; learn more about our certification support services – keep reading for practical insights or speak with one of our consultants.
ISO/IEC 27001:2022 is the latest version of the globally recognised standard for information security management systems (ISMS). It reflects today’s evolving cyber threat landscape and helps organisations implement more precise, risk-based controls to protect their information assets.
What Is ISO 27001?
ISO/IEC 27001 was first published in 2005 by the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission (IEC), evolving from the British standard BS 7799. The latest revision in 2022 strengthens its relevance in today’s digital-first, risk-heavy business environment.
The standard follows the Plan-Do-Check-Act (PDCA) cycle, driving continual improvement in how organisations manage data protection, cyber threats, and regulatory compliance. It provides a structured approach to identifying risks, implementing controls, and safeguarding information assets – whether digital, physical, or intellectual.
ISO 27001 is flexible and scalable, making it suitable for SMEs, public bodies, and global enterprises alike.
Whether pursuing ISO 27001 certification for the first time or transitioning to the 2022 update, mastering its framework turns security compliance into strategic advantage – enhancing customer trust and unlocking new business opportunities where data protection is paramount.
Guide to ISO 27001:2022 Standard Clauses
Scope (Section 1) – This is where we set the playing field for information security. Your organisation needs to protect information in line with legal requirements, customer expectations, and your own policies. Think of it as laying the foundation for a secure and resilient system.
References (Section 2) – Here we connect the dots to ISO/IEC 27000 – the glossary of information security terms that ensures everyone speaks the same security language.
Definitions (Section 3) – No jargon allowed! This section clearly explains all the special terms used throughout the standard, referencing ISO/IEC 27000 for consistency.
Understanding Your Organisation and Its Context (Clause 4) – This is your security reality check. Identify your internal and external issues, stakeholders, and information assets so your security controls align with business needs and risks.
Leadership Commitment (Clause 5) – Security starts at the top! Leadership must actively support the information security management system (ISMS), establish a security culture, and review performance regularly.
Planning Your Approach (Clause 6) – Here’s where we get strategic. Assess risks and opportunities, define information security objectives, and plan how to handle changes or potential security threats.
Support (Clause 7) – Your ISMS needs the right resources to run effectively. This covers competent staff, communication, awareness, and maintaining the proper documentation to support security measures.
Operation (Clause 8) – The action section! Implement and manage security controls across processes, from asset management and access control to incident response and business continuity.
Performance Evaluation (Clause 9) – How do you know it’s working? Regular audits, monitoring, reviews, and reporting ensure your ISMS is effective and meets objectives.
Improvement (Clause 10) – When breaches, gaps, or incidents happen (and they will!), this section guides how to respond, correct root causes, and continually improve your security posture.
Ask us about the certification process
ISO 27001 Consultancy and Certification Companies

ISO 27001 certification means a formal assurance that your organisation has implemented an ISMS that meets the stringent requirements of ISO/IEC 27001.
One of the most important and sometimes confusing aspects of ISO certification is the clear line between consultancies like ours and official certification bodies. This isn’t just industry etiquette – it’s a foundational rule designed to preserve impartiality and prevent conflicts of interest throughout the certification process.
Our role, as ISO 27001 consultants, is to guide you through the entire implementation journey. That includes conducting a gap analysis, mapping out your risk landscape, building tailored policies and controls, and preparing your teams for internal audits.
Certification bodies act as independent assessors. They conduct a formal two-stage audit to verify that your ISMS meets ISO 27001 standards and issue a certificate.
This separation ensures fairness and credibility. We focus entirely on helping you build a resilient, well-documented ISMS, while certification bodies provide objective validation. At Candy Management Consultants, we’re your strategic partners right up to audit day – think of us as your cybersecurity coaches, helping you train for the big match.
The bottom line is, we’ll help you build an exceptional ISO 27001 management system but the final stamp of approval always comes from an accredited or independent ISO certification company.

Explore our implementation service
Why ISO 27001 Certification Matters
While not a legal requirement, being ISO 27001 certified demonstrates your organisation’s commitment to protecting information assets and managing data securely. It reinforces your ability to identify and mitigate information security risks, comply with regulatory demands, and build trust in a marketplace where data protection is critical.
Suitable for organisations of all types and sizes, ISO 27001 compliance enables you to:
Protect sensitive business data and customer personal information
Identify, assess, and control information security risks
Reduce the likelihood and impact of cyber threats or data breaches
Strengthen long-term resilience through continual improvement
Show accountability to clients, partners, and regulators
Avoid costly downtime, fines, and reputational damage
Who Needs ISO 27001?
ISO 27001 is ideal for organisations that want to:
- Protect sensitive information from cyber threats and breaches
- Meet legal, regulatory, or contractual data protection requirements
- Build trust with clients, partners, and stakeholders
- Win contracts in sectors where information security is essential
Popular industries we support:
- Technology – Secure cloud systems, data centres, and digital platforms
- Finance – Protect customer data and ensure regulatory compliance
- Healthcare – Safeguard patient records and manage confidentiality risks
- Professional Services in other sectors – Demonstrate due diligence in handling data
What Are the Benefits of ISO 27001?
Why Regulate Information Security?

Establishing an information security management system through ISO/IEC 27001 delivers measurable value to organisations and their stakeholders. By formalising data protection practices and defining clear security objectives, businesses can reduce risk, maintain confidentiality, and manage sensitive information more effectively.
ISO 27001 certification plays a key role in enabling this. It supports a proactive security culture, encourages continuous improvement, and helps identify vulnerabilities before they become serious threats. This not only protects your organisation’s digital assets but also builds confidence among customers, partners, and regulators.
ISO 27001 is more than just a compliance framework—it’s a recognised symbol of data protection and operational resilience. Many industries, especially those handling personally identifiable information (PII) or financial data, increasingly require suppliers to hold ISO 27001 certification as part of their procurement and risk management processes. Certification from a competent, often UKAS-accredited body provides third-party assurance of your commitment to ISO information security standard.
Adopting ISO 27001 is a strategic investment that supports legal compliance, improves cyber risk management, and reinforces long-term business integrity.

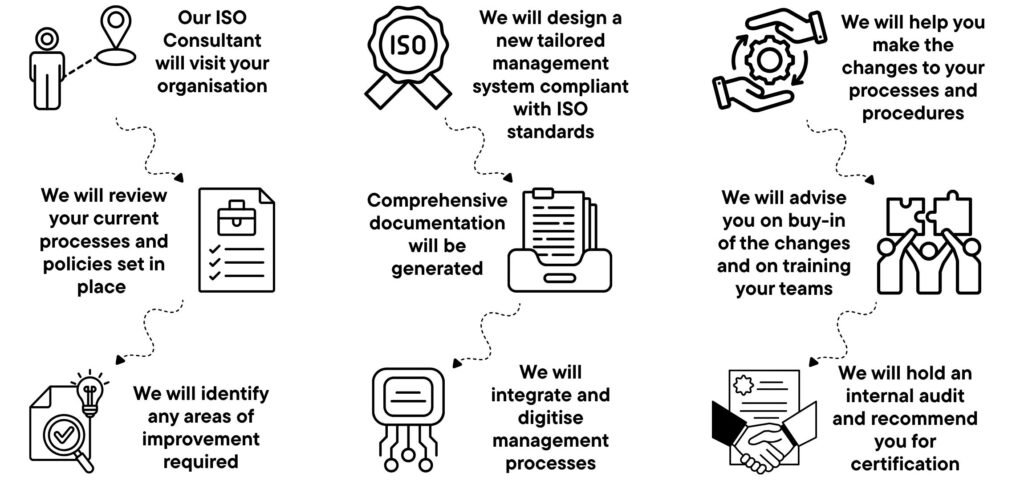
Our 3 Step Process
We make achieving ISO 27001 certification straightforward with a flexible three-step process designed around how you already work. Our trusted method minimises disruption, cuts down costly errors, and simplifies your route to ISO certification—helping you save time, effort, and money.
Keep Up To Date With Our ISO 27001 Blogs
Data Privacy Day: ISO 27001 & Cyber Essentials
If Your Certificate Has Expired A Practical Crisis Management Guide Data Privacy Day is a…
Maintaining ISO/IEC 27001 Certification: What It Really Means for Your Organisation
Maintaining ISO/IEC 27001 Certification Achieving ISO/IEC 27001 certification is a significant milestone for any organisation….
How to Integrate ISO 42001, ISO/IEC 20000-1 and ISO/IEC 27001: A Practical Guide for Modern Organisations
How to Integrate ISO 42001, ISO 20000-1 and ISO 27001 As organisations accelerate their adoption…
What Is ISO 27001 and Why Is It Important for Businesses?
Why is ISO 27001 Important For Businesses? Data is one of the most valuable assets…
ISO/IEC 27001:2022 vs ISO/IEC 27001:2013 — What’s Changed? A Deep Dive
ISO 27001:2022 vs ISO 27001:2013 – What’s Changed? Organisations worldwide are gradually moving to the…
Clause-by-Clause Series: Understanding ISO 27001
Clause-by-Clause Series: Understanding ISO 27001 ISO 27001 is the leading international standard for Information Security…
How Much Does ISO 27001 Certification Cost?
The cost of certification varies depending on:
- The size and complexity of your business
- Number of employees and operational sites
- Number of standards you’re working towards
We charge a competitive day rate and always provide a clear estimate upfront. If fewer consultancy days are needed, you won’t pay for the extras.
Our pricing is simple, honest, and flexible—designed to suit your budget.
Ask about our consultancy price
Why Choose Candy Management Consultants?
Training and Development
We provide businesses with online training courses to support with developing essential skills for daily operations. From leadership to process improvement, our courses provide practical knowledge to enhance efficiency and drive success.
Tailored Solutions
We offer tailored solutions to ensure businesses received ISO support that met their specific needs. By customising our approach, we helped clients achieve and maintain compliance in a way that worked best for them.
Audit Readiness Check
We offer an audit readiness check to help businesses identify gaps, address compliance issues, and ensure they’re fully prepared for their ISO certification audit. This proactive approach reduced stress and increased the chances of a successful outcome.
Digital Transformation
We offer the CandyBox ISO management system to simplify and streamline ISO compliance. Designed for efficiency, it helped businesses manage documents, track progress, and maintain certification with ease.
Payment Plans
We offer payment plans to make ISO certification more accessible and manageable. By spreading the cost over time, we help clients invest in compliance and quality without straining their budgets.
Post Certification Support
We provide post-certification support to help businesses maintain compliance, continuously improve, and prepare for future audits. Our ongoing guidance ensured long-term success beyond certification.
Read happy stories from our clients about how ISO certification helped them achieve business goals after using our services.






